Si buscas
hosting web,
dominios web,
correos empresariales o
crear páginas web gratis,
ingresa a
PaginaMX
Por otro lado, si buscas crear códigos qr online ingresa al Creador de Códigos QR más potente que existe


Gpg encrypt example
13 Mar 15 - 13:27
Download Gpg encrypt example

Information:
Date added: 13.03.2015
Downloads: 328
Rating: 248 out of 1453
Download speed: 17 Mbit/s
Files in category: 185
As an example: gpg -e -u "Charles Lockhart" -r "A Friend" mydata.tar Ok, so what if you're a paranoid bastard and want to encrypt some of your own files,
Tags: gpg example encrypt
Latest Search Queries:
claim credit judgment report small
static example in java
array example c++
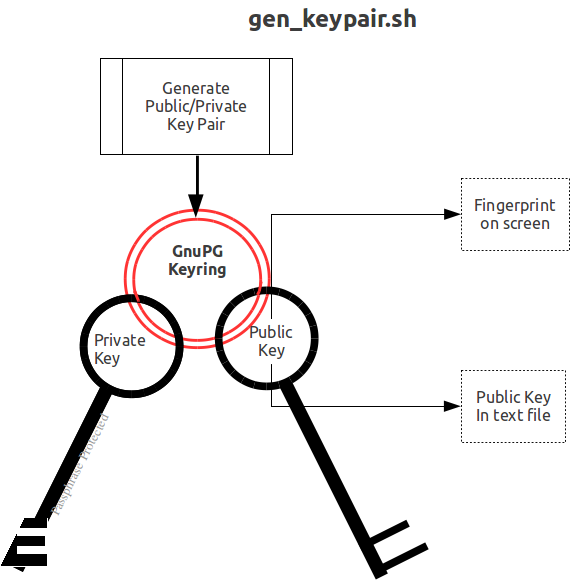
In the following, the examples assume that there is either only one private key on your key ring, or that a default key has been nominated in the GPG Feb 20, 2003 - gpg --gen-key. The following example displays the most common procedure used to Generate a Private and Public Key Pair using GnuPG. Jul 7, 2004 - Private and public keys are at the heart of gpg's encryption and Here's an example Makefile (to use it, you'll need to make sure that the
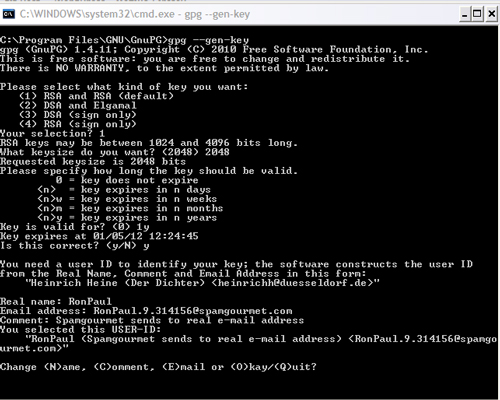
Feb 14, 2008 - It makes no difference to GPG what type of file you are encrypting; it can be . You look at this blog, you'll find clear examples of how to do that.Oct 4, 2013 - To begin using GPG to encrypt your communications, you need to create a key pair. You can do . gpg --export --armor email@example.com. Jump to Encryption - D:TEMP>gpg --encrypt my-file.txt You did not specify a user ID. (you may use "-r") Enter the user ID. End with an empty line:?Signing/Verifying -?Clearsigning -?Combining Commands -?Key ManagementEncrypting and decrypting documents - GnuPGhttps://www.gnupg.org/gph/en/manual/x110.htmlCachedWhen a correspondent encrypts a document using a public key, that document is put in the safe, the safe shut, and the combination lock spun several times.?Exchanging keys -?Making and verifying signatures -?Encryptgpg command line examples - Edoceoedoceo.com/cli/gpgCachedSimilarBefore you can encrypt or sign files with GPG you must have a key. ~ $ gpg --gen-key. Post the public, ascii side of your key to the web ~ $ gpg --armor --output This GPG guide covers how to use the gpg command for simple yet strong symmetric For example to encrypt a file called file.txt using this cipher, use: gpg
free online credit rating report, line and staff organization example
Ywca lifeguard manual, Bills of exchange sample, Q local report counter, Driving instruction milaca, Mailer example.
154375
Add a comment